Firewall
All about firewall.
Firewalls can be an effective means of protecting a local system or network of systems from network-based security threats while at the same time affording access to the outside world via wide area networks and the Internet. Moreover, the firewall is also in charge of following up, analyzing information flow and starting the decision-making process with the mentioned above information.
Goals of a firewall:
- All traffic from inside to outside and vice versa must pass through the firewall.
- Only authorized traffic, as defined by the local security policy, will be allowed to pass.
- The firewall itself is immune to penetration.
1. Firewall Characteristics and access policy
A critical component in the planning and implementation of a firewall is specifying a suitable access policy. Lists a range of characteristics that a firewall access policy could use to filter traffic, including:
-
IP Address and Protocol Values: Controls access based on the source or destination addresses and port numbers, direction of flow being inbound or outbound, and other network and transport layer characteristics. It is typically used to limit access to specific services.
-
Application Protocol: Controls access on the basis of authorized application protocol data. This type of filtering is used by an application-level gateway that relays and monitors the exchange of information for specific application protocols.
-
User Identity: Controls access based on the users identity, typically for inside users who identify themselves using some form of secure authentication technology, such as IPSec.
-
Network Activity: Controls access based on considerations such as the time or request, e.g., only in business hours; rate of requests, e.g., to detect scanning attempts; or other activity patterns.
2. Types of Firewalls
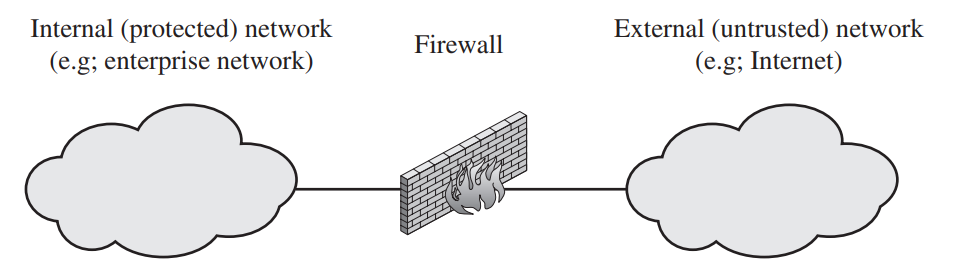 A firewall can monitor network traffic at a number of levels, from low-level network packets, either individually or as part of a flow, to all traffic within a transport connection, up to inspecting details of application protocols. The choice of which
level is appropriate is determined by the desired firewall access policy. Depending on the type of firewall, it may examine one or more protocol headers in each packet, the payload of each packet, or the pattern generated by a sequence of
packets. In this section, we look at the principal types of firewalls:
A firewall can monitor network traffic at a number of levels, from low-level network packets, either individually or as part of a flow, to all traffic within a transport connection, up to inspecting details of application protocols. The choice of which
level is appropriate is determined by the desired firewall access policy. Depending on the type of firewall, it may examine one or more protocol headers in each packet, the payload of each packet, or the pattern generated by a sequence of
packets. In this section, we look at the principal types of firewalls:
- Packet filtering firewall
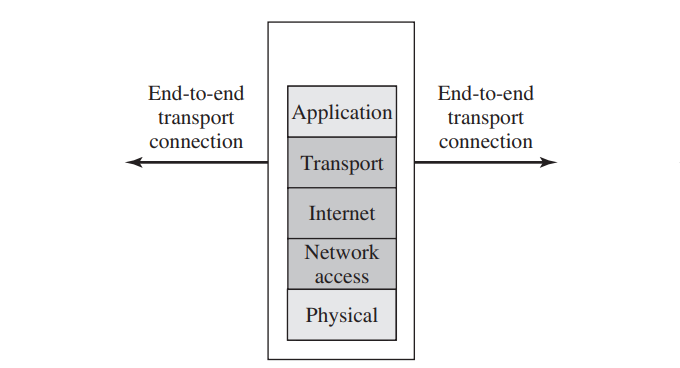
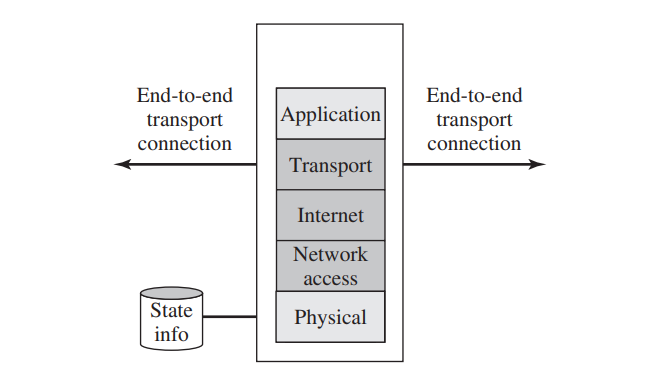
- Stateful inspection firewall
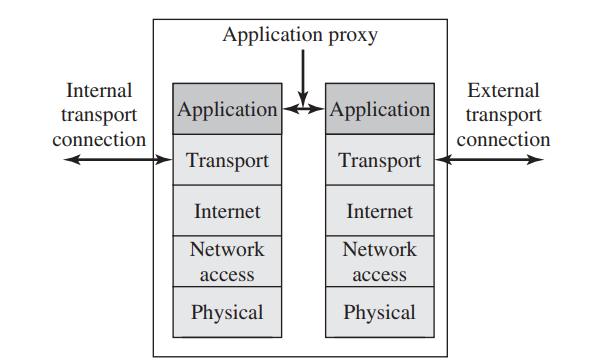
- Application proxy firewall
- Circuit-level proxy firewall
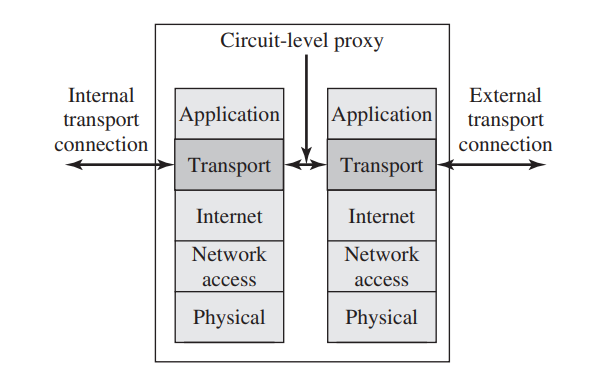
3. Firewall Basing
3.1 Bastion Host
A bastion host is a system identified by the firewall administrator as a critical strong point in the network’s security. Typically, the bastion host serves as a platform for an application-level or circuit-level gateway. Common characteristics of a bastion host are as follows:
-
Only services that a network administrator considers are installed are installed on basting hosts, such as DNS, FTP, HTTP, SMTP, etc.
-
Basting hosts may require additional authentication before the user is allowed to access proxy services. Additionally, each proxy service may require its authentication before granting access to the user
-
Each proxy is configured to support only a set of standard command sets.
-
Each proxy is configured to access only to a specific server. This means that commands/features set may be applied only to a subset of systems on the protected network.
-
Each proxy maintains a detailed inspection by logging all traffic, the duration of each connection. This record of access information is essential to investigate and stop attacks by intruders.
-
Each proxy module is a tiny software package specifically designed for network security. Due to its simplicity, it is easier to check for security errors. For example, a mail application in UNIX may contain more than 20,000 lines of code, while a proxy mail may have fewer than 1,000 lines.
-
Each proxy is independent of other proxies on the bastion host. If there is a problem with the operation of any proxy, or if a future vulnerability is discovered, it can be uninstalled without affecting the operation of the other proxy applications. Also, if the user population requires support for a new service, the network administrator can easily install the required proxy on the bastion host.
-
A proxy generally performs no disk access other than to read its initial configuration file. Hence, the portions of the file system containing executable code can be made read-only. This makes it difficult for an intruder to install Trojan horse sniffers or other dangerous files on the bastion host.
-
Each proxy runs as a user without privileges on a private directory and is secured on the host bastion.
3.2 Host-Based Firewalls
The host-based firewall is an application module that protects individual servers. Such modules are usually available in the operating system or provided as additional packages. Like a regular firewall, host-resident filters and restricts data flows. Some advantages of using a server-based or workstation-based firewall:
-
Information filtering rules are customizable for each server. It is possible to deploy specific security policies for each enterprise with different filters for each different server.
-
Protection is provided independently of the topology. Thus both internal and external attacks must pass through the firewall.
-
Used in conjunction with stand-alone firewalls, the host-based firewall provides an additional layer of protection. A new type of server can be added to the network, with its own firewall, without the necessity of altering the network firewall configuration.
3.3 Personal Firewall
The personal firewall controls the information traffic of a personal computer or a workstation on one side and the Internet or enterprise network on the other side. Personal firewall functionality can be used in the home environment and on corporate intranets. Typically, a personal firewall is an application. In case there are many computers connect to the Internet, firewall functionality can also be housed in a router. Personal firewalls are often more complicated than server-based firewalls or independent firewalls. The primary role of the personal firewall is to deny unauthorized access to the network. The firewall can also monitor activity for scanning or detecting malware.
4. Firewall configuration
A network administrator must determine the location and number of firewalls needed, and here are some typical options:
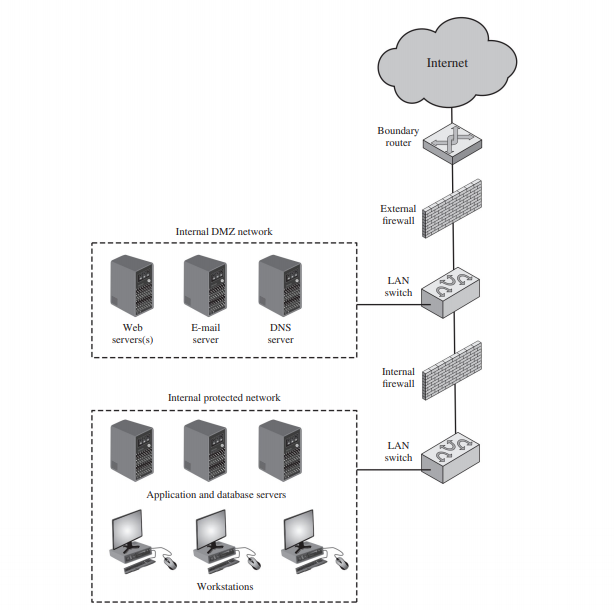
4.1 DMZ Networks:
An external firewall is placed at the edge of a local or enterprise network, just inside the boundary router that connects to the Internet or some wide area network (WAN). One or more internal firewalls protect the bulk of the enterprise network. Between these two types of firewalls are one or more networked devices in a region referred to as a DMZ (demilitarized zone) network. Systems that are externally accessible but need some protections are usually located on DMZ networks. Typically, the systems in the DMZ require or foster external connectivity, such as a corporate Web site, an e-mail server, or a DNS (domain name system) server.
The external firewall provides a measure of access control and protection for the DMZ systems consistent with their need for external connectivity. The external firewall also provides a basic level of protection for the remainder of the enterprise network.
Internal firewalls serve three purposes:
-
The internal firewall adds more stringent filtering capability, compared to the external firewall, in order to protect enterprise servers and workstations from external attack.
- The internal firewall provides two-way protection with respect to the DMZ.
- First, the internal firewall protects the remainder of the network from attacks launched from DMZ systems.
- Second, an internal firewall can protect the DMZ systems from attack from the internal protected network.
- Multiple internal firewalls can be used to protect portions of the internal network from each other.
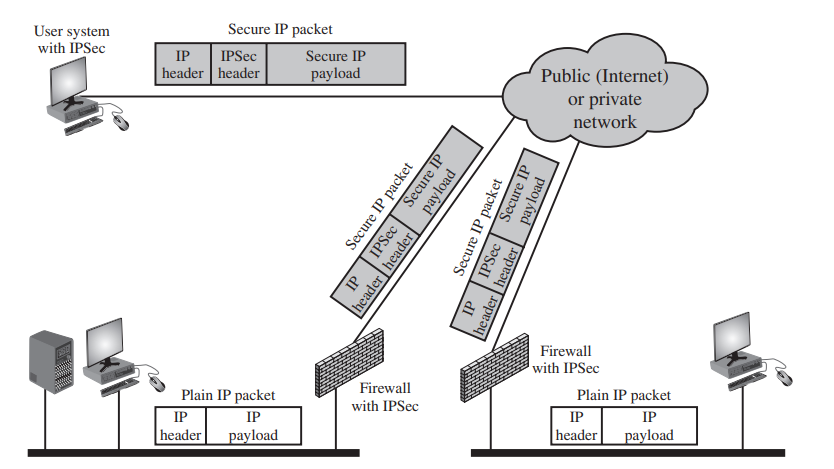
4.2 Virtual Private Networks:
In essence, a VPN uses encryption and authentication in the lower protocol layers to provide a secure connection through an otherwise insecure network, typically the Internet. VPNs are generally cheaper than real private networks using private lines but rely on having the same encryption and authentication system at both ends. The encryption may be performed by firewall software or possibly by routers. The most common protocol mechanism used for this purpose is at the IP level and is known as IPSec
If IPSec is implemented in a separate box behind (internal to) the firewall, then VPN traffic passing through the firewall in both directions is encrypted. In this case, the firewall is unable to perform its filtering function or other security functions, such as access control, logging, or scanning for viruses. IPSec could be implemented in the boundary router, outside the firewall. However, this device is likely to be less secure than the firewall and thus less desirable as an IPSec platform
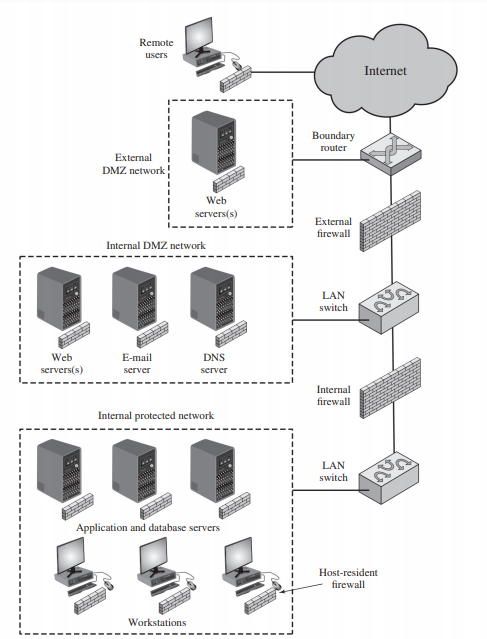
4.3 Distributed Firewalls
A distributed firewall configuration involves stand-alone firewall devices plus hostbased firewalls working together under a central administrative control. Administrators can configure hostresident firewalls on hundreds of servers and workstation as well as configure personal firewalls on local and remote user systems. Tools let the network administrator set policies and monitor security across the entire network. These firewalls protect against internal attacks and provide protection tailored to specific machines and applications. Stand-alone firewalls provide global protection, including internal firewalls and an external firewall, as discussed previously.
With distributed firewalls, it may make sense to establish both an internal and an external DMZ. Web servers that need less protection because they have less critical information on them could be placed in an external DMZ, outside the external firewall. What protection is needed is provided by host-based firewalls on these servers
An important aspect of a distributed firewall configuration is security monitoring. Such monitoring typically includes log aggregation and analysis, firewall statistics, and fine-grained remote monitoring of individual hosts if needed.
reference
Stallings, W., & Brown, L. (2015). Computer Security Principles and Practice (3rd Edition).